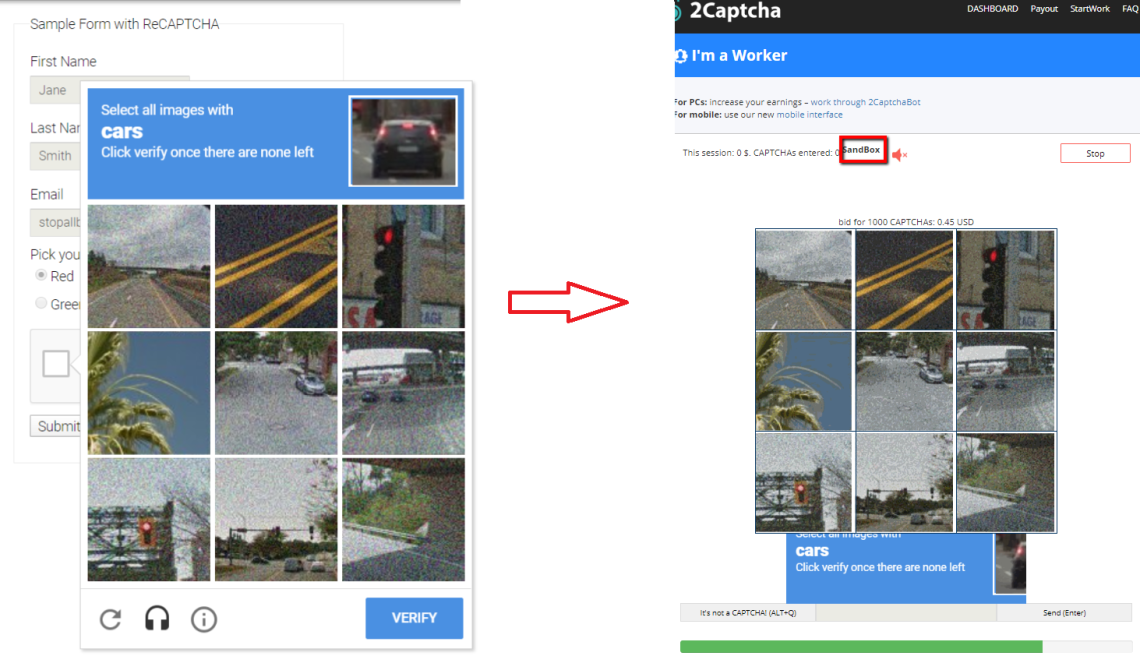
In the age of digital security, CAPTCHAs have become ubiquitous guardians of online gateways, protecting websites from malicious bots and automated attacks. Among the diverse array of funcaptcha solver implementations, Funcaptcha stands out as a particularly robust defense mechanism. However, as with any security measure, its efficacy relies on staying one step ahead of those seeking to bypass it. In this exploration, we delve into the realm of Funcaptcha, uncovering the methods behind its design and the secrets of those who seek to decode it.
Understanding Funcaptcha
Funcaptcha, short for “Functional CAPTCHA,” is an innovative solution developed by the team at Arkose Labs. Unlike traditional text-based CAPTCHAs, Funcaptcha presents users with interactive challenges that require human-like intelligence to solve. These challenges typically involve tasks such as rotating objects, identifying specific elements within an image, or completing simple puzzles.
The underlying principle behind Funcaptcha is to create puzzles that are easy for humans to solve but difficult for automated bots to crack. By leveraging human cognitive abilities such as pattern recognition, spatial reasoning, and logical deduction, Funcaptcha effectively separates humans from bots.
The Arms Race: Decoding Funcaptcha
Despite its robust design, Funcaptcha is not immune to attempts at decoding by malicious actors. The arms race between security measures and those seeking to bypass them is a constant struggle in the realm of cybersecurity. As Funcaptcha gains popularity and widespread adoption, so too does the interest in circumventing its defenses.
Unlocking Solver Secrets
Decoding Funcaptcha requires a deep understanding of its underlying mechanisms and vulnerabilities. Researchers and hackers alike employ various techniques to analyze and reverse-engineer Funcaptcha puzzles, seeking ways to automate the solving process.
One approach involves utilizing machine learning algorithms to train models capable of recognizing and solving Funcaptcha challenges. By feeding these algorithms with large datasets of Funcaptcha puzzles and their corresponding solutions, researchers can train models to mimic human problem-solving abilities.
Another method involves analyzing the structure and patterns present in Funcaptcha challenges. By identifying common elements and recurring themes across different puzzles, researchers can develop algorithms that exploit these patterns to automate the solving process.
Furthermore, collaborative efforts within the cybersecurity community play a crucial role in decoding Funcaptcha. Forums, chat groups, and online communities serve as platforms for sharing insights, techniques, and findings related to Funcaptcha decoding. By pooling together knowledge and expertise, researchers can accelerate the process of unraveling Funcaptcha’s secrets.
The Ethical Dilemma
While the quest to decode Funcaptcha may be driven by curiosity, academic research, or even noble intentions to improve cybersecurity, it raises ethical considerations. The line between ethical research and malicious intent can often blur in the realm of cybersecurity. What begins as an academic pursuit to understand and strengthen security measures can easily be co-opted by malicious actors for nefarious purposes.
As researchers uncover vulnerabilities in Funcaptcha, they face the ethical dilemma of how to responsibly disclose their findings. While disclosing vulnerabilities to the appropriate authorities can lead to improvements in security measures, it also runs the risk of empowering malicious actors with the knowledge needed to exploit these vulnerabilities.
Conclusion
Funcaptcha represents a significant advancement in the field of CAPTCHA technology, leveraging interactive challenges to thwart automated bots and enhance online security. However, as with any security measure, its effectiveness is not absolute and is subject to ongoing scrutiny and attempts at circumvention.